1、我们要构造一个简易版蜜罐,代码如下:
import subprocess
from flask import Flask
from flask import request
import sys
app = Flask(__name__)
@app.route('/')
def ip():
ip = request.remote_addr
command = f"firewall-cmd --permanent --ipset=blacklist --add-entry={ip}"
try:
subprocess.run(command, shell=True, check=True)
subprocess.run("firewall-cmd --reload", shell=True, check=True)
print(f"{command}命令执行成功!")
print(f"阻止来着互联网{ip}的端口扫描。")
except subprocess.CalledProcessError as e:
print(f"{command}命令执行失败,错误信息: {e}")
return ip
if __name__ == "__main__":
# app.run(host="0.0.0.0", port=sys.argv[1])
app.run(host="0.0.0.0", port=8443, debug=False)
2、启动一个 screen 会话,运行简易版蜜罐,蜜罐端口为 8443
[root@VM-24-14-centos honey-pot]# python honey-pot.py
* Serving Flask app 'honey-pot'
* Debug mode: off
WARNING: This is a development server. Do not use it in a production deployment. Use a production WSGI server instead.
* Running on all addresses (0.0.0.0)
* Running on http://127.0.0.1:8443
* Running on http://10.0.24.14:8443
Press CTRL+C to quit
3、配置防火墙策略:
3.1 创建ipset
# firewall-cmd --permanent --zone=public --new-ipset=blacklist --type=hash:net
执行完命令可在/etc/firewalld/ipsets路径下看到生成的blacklist.xml文件。
# ls /etc/firewalld/ipsets
blacklist.xml honey-pot-ip.xml honey-pot-net.xml
3.2 封禁ipset
firewall-cmd --permanent --zone=public --add-rich-rule="rule family=ipv4 source ipset=blacklist drop"
firewall-cmd --reload
3.3 firewalld ipset维护命令
列出所有ipset
firewall-cmd --get-ipsets
列出set下所有的entry
firewall-cmd --ipset=blacklist --get-entries
打印set的路径
firewall-cmd --permanent --path-ipset=blacklist
删除set
firewall-cmd --permanent --delete-ipset=blacklist
4、测试:
4.1、在一台云服务器上访问其8443端口:第一次成功访问
(py3) [root@VM-24-15-centos ~]# wget 101.42.5.97:8443
--2024-01-21 09:27:06-- http://101.42.5.97:8443/
正在连接 101.42.5.97:8443... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:12 [text/html]
正在保存至: “index.html”
index.html 100%[==================================================================================>] 12 --.-KB/s 用时 0.001s
2024-01-21 09:27:07 (17.8 KB/s) - 已保存 “index.html” [12/12])
(py3) [root@VM-24-15-centos ~]#
4.2、在服务器侧,监控Flask运行日志:
[root@VM-24-14-centos honey-pot]# firewall-cmd --reload
success
[root@VM-24-14-centos honey-pot]# firewall-cmd --ipset=blacklist --get-entries
192.168.100.0/24
[root@VM-24-14-centos honey-pot]# python honey-pot.py
* Serving Flask app 'honey-pot'
* Debug mode: off
WARNING: This is a development server. Do not use it in a production deployment. Use a production WSGI server instead.
* Running on all addresses (0.0.0.0)
* Running on http://127.0.0.1:8443
* Running on http://10.0.24.14:8443
Press CTRL+C to quit
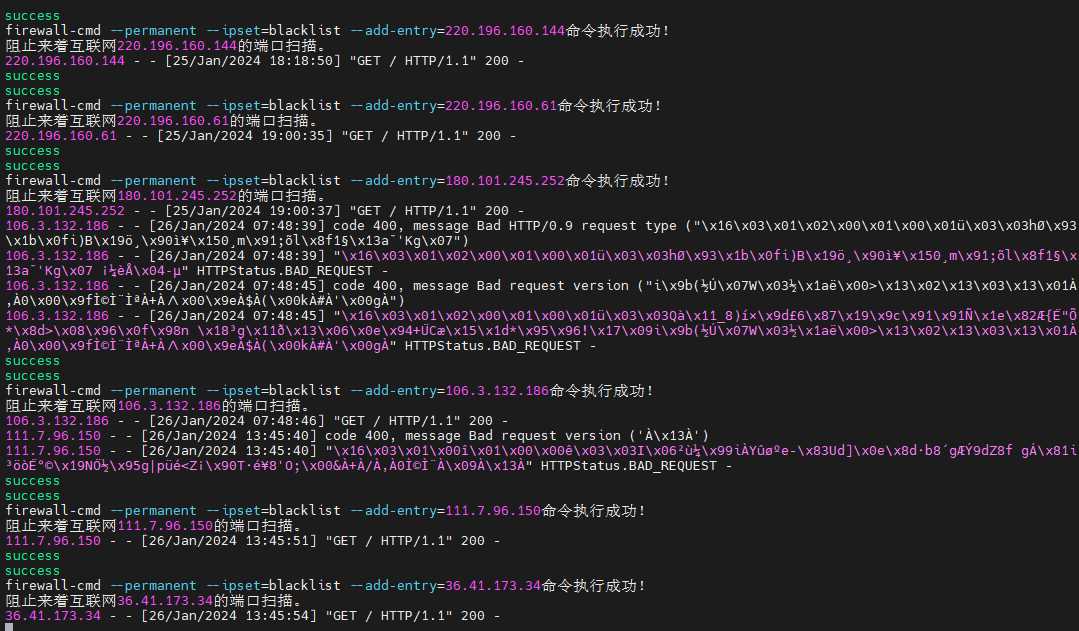
success
success
firewall-cmd --permanent --ipset=blacklist --add-entry=101.42.230.2命令执行成功!
阻止来着互联网101.42.230.2的端口扫描。
101.42.230.2 - - [21/Jan/2024 09:27:07] "GET / HTTP/1.1" 200 -
4.3、在一台云服务器上访问其8443端口:第2次成功失败:
(py3) [root@VM-24-15-centos ~]# wget 101.42.5.97:8443
--2024-01-21 09:27:06-- http://101.42.5.97:8443/
正在连接 101.42.5.97:8443... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:12 [text/html]
正在保存至: “index.html”
index.html 100%[==================================================================================>] 12 --.-KB/s 用时 0.001s
2024-01-21 09:27:07 (17.8 KB/s) - 已保存 “index.html” [12/12])
(py3) [root@VM-24-15-centos ~]# wget 101.42.5.97:8443
--2024-01-21 09:29:19-- http://101.42.5.97:8443/
正在连接 101.42.5.97:8443...
^C
(py3) [root@VM-24-15-centos ~]# telnet 101.42.5.97 8443
Trying 101.42.5.97...
^C
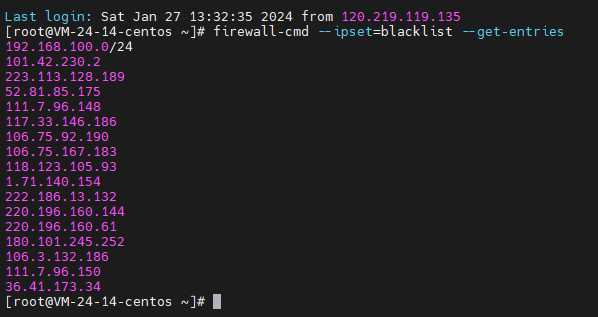
4.4、在服务器端查看当前封堵的IP地址:
[root@VM-24-14-centos ~]# firewall-cmd --ipset=blacklist --get-entries
192.168.100.0/24
101.42.230.2
[root@VM-24-14-centos ~


文章评论